|
|
| Something About the Kozinski Story You Didn't Read in the LA Times |
 |
|
Friday, June 13 2008 @ 01:46 PM EDT
|
First, this is off topic for Groklaw. I know. But I have some information about the Kozinski story that I'm not seeing reported. I provided it to the LA Times yesterday. Seeing it not reported there today, and factoring in that the email might have been caught in a spam catcher, I will provide it here myself.
There is some evidence I found on Internet Archive that indicates to me that the judge was apparently truthful in saying that the site in question was intended to be private, which I will show you for your consideration. Second, I think it's important to highlight that the person who "tipped off" the LA Times reporter has been, I gather, in a kind of feud with Kozinski for some time. According to the ABA Journal, he has been monitoring the Kozinski site: AP spoke to Beverly Hills, Calif., attorney Cyrus Sanai, who said he had told the Los Angeles Times about the images on the Kozinski website. He said he found them while monitoring the site as part of a dispute with the 9th Circuit in connection with his parents’ divorce. He said he contacted reporters at various publications since January in an effort to expose them. You can read about what they each, Kozinski and Sanai, wrote on a dispute between them here. It raises a question in my mind about whether or not this is just about the divorce. But my next question would be, if this was intended as a private site, would it be legal for an uninvited person to enter and monitor it? Exactly how would that work, given the Computer Fraud and Abuse Act, not to mention any local California laws regarding privacy and computer integrity? We know there are such laws in California, from the HP-reporters scandal.
Here's what I found on Internet Archive. If you search for the site, www.alex.kozinski.com , this is what you find:
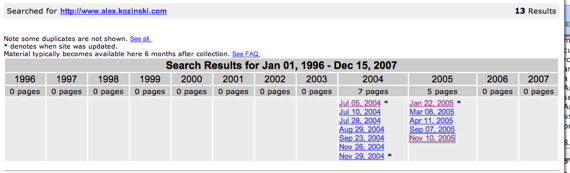
Do you see how it ends in 2005? That would indicate that at that point, someone took steps to make sure that bots couldn't crawl the site, that it was intended to be a private site. So what happened? I don't know, but I have a possible theory. I suspect that they may not have realized that blocking a homepage doesn't necessarily block subdirectories. Let me show you why I think that could be it. If you click on any of the pages in the archive, you find this:

If you saw that message, would you assume that you were supposed to monitor the site? That it was OK to enter and look around? The only way to see anything on the site was to add a subdirectory, like /stuff. Incidentally, if you want to see what was behind the message to get lost back in 2005, here's the list of all the hidden pages, back when the Archive was collecting them, and there is nothing there at all untoward that I could find. Mr. Sanai might have found this PDF annoying, I gather from this entry in Patterico's Pontifications, a blog by a prosecutor in California, who is providing a lot of details about the feud. That PDF is a partial transcript of a motion hearing, revealing that Sinai sued a judge, not named in the transcript, who apparently recused himself from the divorce case, while complaining about the family's conduct:
Sanai told me that he filed a complaint alleging misconduct by Kozinski for commenting on a pending case — Sanai’s petition for rehearing en banc of a legal issue related to his parents’ divorce. Sanai also complained that Kozinski had put materials related to the case on Kozinski’s web site. This, Kozinski clearly did. Howard Bashman has preserved Kozinski’s piece about Sanai. It purports to link a .pdf critical of Sanai. You can see the link by right-clicking the hyperlink in Kozinski’s piece that says “(read the PDF)” and checking “properties.” It goes to this link: http://alex.kozinski.com/judge.thibodeau.pdf.
When the Ninth Circuit’s Judicial Council finally ruled on Sanai’s complaint, it was in this order [PDF]. It found no misconduct on the unnamed judge’s part, but noted that the judge had nevertheless apologized for any appearance of impropriety. The PDF was in Kozinski's private collection. I know. The story is mighty strange. Regarding the site monitoring, I can't help but wonder what the prosecutor would say to doing this, written, he says, by Sanai in a comment on the blog: While his son did register the site and set up its architecture–I found an outline of the code on his portion of kozinski.com–it was Judge Kozinski who had complete control of the sub-domain alex.kozinski.com. We'll find out from the investigation if that part is so, but if it is, exactly who has the right to fumble through a private site's code, take data, and share it with others? Are there not laws about that?
Larry Lessig on the Kozinkski mess: Here are the facts as I've been able to tell: For at least a month, a disgruntled litigant, angry at Judge Kozinski (and the Ninth Circuit) has been talking to the media to try to smear Kozinski. Kozinski had sent a link to a file (unrelated to the stuff being reported about) that was stored on a file server maintained by Kozinski's son, Yale. From that link (and a mistake in how the server was configured), it was possible to determine the directory structure for the server. From that directory structure, it was possible to see likely interesting places to peer. The disgruntled sort did that, and shopped some of what he found to the news sources that are now spreading it.
Cyberspace is weird and obscure to many people. So let's translate all this a bit: Imagine the Kozinski's have a den in their house. In the den is a bunch of stuff deposited by anyone in the family -- pictures, books, videos, whatever. And imagine the den has a window, with a lock. But imagine finally the lock is badly installed, so anyone with 30 seconds of jiggling could open the window, climb into the den, and see what the judge keeps in his house. Now imagine finally some disgruntled litigant jiggers the lock, climbs into the window, and starts going through the family's stuff. He finds some stuff that he knows the local puritans won't like. He takes it, and then starts shopping it around to newspapers and the like: "Hey look," he says, "look at the sort of stuff the judge keeps in his house."...
This analogy, I submit, fits perfectly the alleged scandal around Kozinski. His son set up a server to make it easy for friends and family to share stuff -- family pictures, documents he wanted to share, videos, etc. Nothing alleged to have been on this server violates any law. (There's some ridiculous claim about "ibiblio.org." But the video is not ibiblio.org. It lives today on YouTube -- a funny (to some) short of a man defecating in a field, and then being chased by a donkey. If there was malicious intent in this video, it was the donkey's. And in any case, nothing sexual is shown in that video at all.) No one can know who uploaded what, or for whom. The site was not "on the web" in the sense of a site open and inviting anyone to come in. It had a robots.txt file to indicate its contents were not to be indexed. That someone got in is testimony to the fact that security -- everywhere -- is imperfect. But this was a private file server, like a private room, hacked by a litigant with a vendetta. Decent people -- and publications -- should say shame on the person violating the privacy here, and not feed the violation by forcing a judge to defend his humor to a nosy world. I'm remembering the California laws that came up in the HP pretexting story. Remember this? Specifically, Lockyer said, the HP case runs afoul of California Penal Code Section 502, which prohibits "tampering, interference, damage, and unauthorized access to lawfully created computer data and computer systems." Here's California Penal Code Section 502, for your reading pleasure. I wrote about it before, in the HP connection, editing out the bits that didn't seem relevant. The part that seems to me, at least, and my non-lawyer brain to perhaps be relevant is this: (a) It is the intent of the Legislature in enacting this section to expand the degree of protection afforded to individuals, businesses, and governmental agencies from tampering, interference, damage, and unauthorized access to lawfully created computer data and computer systems. The Legislature finds and declares that the proliferation of computer technology has resulted in a concomitant proliferation of computer crime and other forms of unauthorized access to computers, computer systems, and computer data.
The Legislature further finds and declares that protection of the integrity of all types and forms of lawfully created computers, computer systems, and computer data is vital to the protection of the privacy of individuals as well as to the well-being of financial institutions, business concerns, governmental agencies, and others within this state that lawfully utilize those computers, computer systems, and data....
(c) Except as provided in subdivision (h), any person who commits any of the following acts is guilty of a public offense:
(1) Knowingly accesses and without permission alters, damages, deletes, destroys, or otherwise uses any data, computer, computer system, or computer network in order to either (A) devise or execute any scheme or artifice to defraud, deceive, or extort, or (B) wrongfully control or obtain money, property, or data.
(2) Knowingly accesses and without permission takes, copies, or makes use of any data from a computer, computer system, or computer network, or takes or copies any supporting documentation, whether existing or residing internal or external to a computer, computer system, or computer network.
(3) Knowingly and without permission uses or causes to be used computer services.
As I say, I'm no lawyer, but if that doesn't apply, could someone please explain to me why it doesn't? I suppose you could defend by saying you thought it was public, and that's just the flip side of what Kozinski is saying, that he thought it wasn't. Plenty of ickiness to go around, to my eyes. But the Internet Archive material rebuts any attempt to claim, as apparently has been claimed, that the site was taken down and then restored after the dispute regarding the divorce. Apparently, the intent was to take it private forever. And without implying anything, if it were me, I'd want to investigate who uploaded content. After all, someone who can read someone's code can probably do a great deal more than that, so hopefully the investigation will include such things. Now, I'm no fan of porn, and I don't find it funny, but there seems to be more to this story than immediately meets the eye. I've been smeared, and I know how it feels. And fair is fair. It's what Groklaw is about, fairness, and to tell you the rest of the story when the mainstream media doesn't.
Update: Mrs. Kozinski speaks, and the LA Times responds to criticism. There is a rather speedy committee of judges from the 3rd Circuit set up to investigate the matter:
And now, in a statement on the U.S. Courts website for the federal judiciary, the chairman of the 3rd Circuit's judicial council names the members of the special committee who will investigate In Re Complaint of Judicial Misconduct, No. 08-90035.
They are: 3rd Circuit Chief Judge Scirica, who chairs the circuit's judicial council; Judge Marjorie Rendell and Judge Walter Stapleton, both of the 3rd Circuit; Chief District Judge Harvey Bartle III, of the Eastern District of Pennsylvania; and Chief District Judge Garrett Brown Jr. of the District of New Jersey.
|
|
|
|
| Authored by: TheBlueSkyRanger on Friday, June 13 2008 @ 02:02 PM EDT |
Dobre utka,
The Blue Sky Ranger[ Reply to This | # ]
|
| |
| Authored by: TheBlueSkyRanger on Friday, June 13 2008 @ 02:03 PM EDT |
Dobre utka,
The Blue Sky Ranger[ Reply to This | # ]
|
- Fake Steve Jobs leaving Forbes - Authored by: Anonymous on Friday, June 13 2008 @ 03:26 PM EDT
- rish Voters Appear to Reject Treaty on Europe - Authored by: jeevesbond on Friday, June 13 2008 @ 10:32 PM EDT
- Becta - Authored by: Anonymous on Saturday, June 14 2008 @ 12:28 PM EDT
- Becta - Authored by: Vic on Saturday, June 14 2008 @ 12:48 PM EDT
- Becta - Authored by: Anonymous on Saturday, June 14 2008 @ 04:00 PM EDT
- And I get the impression - Authored by: Anonymous on Saturday, June 14 2008 @ 05:00 PM EDT
- ISO process slammed (Durusau: Here he goes again) - Authored by: PolR on Saturday, June 14 2008 @ 02:00 PM EDT
- NP: Trend Micro: Barracuda Suit Not About Open Source - Authored by: Ted Powell on Saturday, June 14 2008 @ 02:40 PM EDT
- Microsoft releases first Open XML SDK - Authored by: Anonymous on Saturday, June 14 2008 @ 03:08 PM EDT
- TFS Gateway Prior Art to TrendMicro '600 Patent - Authored by: GFransson on Monday, June 16 2008 @ 05:56 PM EDT
| |
| Authored by: TheBlueSkyRanger on Friday, June 13 2008 @ 02:04 PM EDT |
Dobre utka,
The Blue Sky Ranger[ Reply to This | # ]
|
- Hat Trick! - Authored by: TheBlueSkyRanger on Friday, June 13 2008 @ 02:06 PM EDT
- 3/3 and 60secs between - Authored by: Anonymous on Friday, June 13 2008 @ 02:16 PM EDT
- OT: Deposition--Texas style - Authored by: Ted Powell on Friday, June 13 2008 @ 03:21 PM EDT
- Globe and Mail - Ottawa gets tough with illegal downloaders - Authored by: Anonymous on Friday, June 13 2008 @ 04:27 PM EDT
- Tim Russert, NBC News, passes away at work - Authored by: hardmath on Friday, June 13 2008 @ 04:27 PM EDT
- AP v. Internets - Authored by: Anonymous on Friday, June 13 2008 @ 04:43 PM EDT
- grad students with too much time on their hand? - Authored by: Anonymous on Friday, June 13 2008 @ 06:42 PM EDT
- Judge declares mistrial in LA obscenity case - Authored by: SpaceLifeForm on Friday, June 13 2008 @ 07:21 PM EDT
- ODF alliance applauds EU Commision's statement - Authored by: Anonymous on Saturday, June 14 2008 @ 01:59 AM EDT
- The "Unix Conspiracy" - Authored by: Anonymous on Saturday, June 14 2008 @ 03:31 AM EDT
- NY Justice orders himself a payraise - Authored by: Anonymous on Saturday, June 14 2008 @ 10:01 AM EDT
- Whoops... - Authored by: Anonymous on Saturday, June 14 2008 @ 10:50 AM EDT
- BECTA Rubbishes Almost the Entire UK Open Source Industry - Authored by: micheas on Saturday, June 14 2008 @ 02:11 PM EDT
- ;) = Truth is Fiction = Fiction is Truth = Truth is Truth ? - Authored by: Anonymous on Saturday, June 14 2008 @ 02:19 PM EDT
| |
| Authored by: ThrPilgrim on Friday, June 13 2008 @ 02:09 PM EDT |
The problem is that if it's meant to be privet then you really need at least
basic authentication.
Security by obscurity just does not work.[ Reply to This | # ]
|
| |
| Authored by: kutulu on Friday, June 13 2008 @ 02:20 PM EDT |
I'm positive there have been multiple precedents in this area but I can't think
of any specific names (I'll go look them up after work if no one else has).
But my recollection is that, if the site is accessible from the outside then
it's not "private", regardless of the owner's intent, at least not in
the sense that computer abuse laws consider it. It's pretty easy to hop onto
Google and find tons of images and documents that people threw onto their
personal home pages and thought would be private but weren't. Many people
falsely assume that, when they take out the index.html page from a directory,
that it becomes inaccessible. In fact, that depends on how the web server is
configured (apache has a NoIndex option) -- and even then, if you know a file
name in the folder you can still see it.
Of course, we don't know how much other access control the judge had in place --
even something as simple as basic plaintext authentication or a simple PHP forms
log-in would probably qualify as sufficient access control to trigger a computer
fraud/abuse style law.
[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 02:23 PM EDT |
Didn't SCO claim that IBM hacked its way onto SCO's server to gather evidence?
Was there a ruling?
[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 02:27 PM EDT |
This is so wrong. There can be no privacy expected on a publicly accessible web
site. If privacy is wanted, authentication of some sort needs to be set up. Just
because a site isn't indexed, doesn't mean it's "private". That's just
nuts.
The window/faulty lock analogy is so wrong. A correct analogy would be more like
depositing the stuff in the street and then being upset when people stop to look
at what's there.
[ Reply to This | # ]
|
| |
| Authored by: joe on Friday, June 13 2008 @ 02:30 PM EDT |
If you want something private, and keep it on the Web, add authentication.
Anything else can be detected.
Oh, and if using Basic Auth, run it over https.
In this case, my guess would be that some directory didn't have an index.html or
similar. The default then is for the Webserver to display the files and
subdirectories in that directory. This is not snooping or anything, this is just
how it works. Anybody who configures web servers should know that.
[ Reply to This | # ]
|
| |
| Authored by: bbaston on Friday, June 13 2008 @ 02:46 PM EDT |
| For Groklaw's benefit - whether participating over at OASIS or just passing by -
here's the place to post.
PJ reminds those of us monitoring the discussion
to
"Stay polite at all times, of course, if you say anything,
and you needn't say anything, but do follow along and please keep us posted on
anything you see that sounds peculiar."
OASIS
discussion list for ODF Implementation, Interoperability and
Conformance
Some relevent OASIS announcements include the ones here and her
e.
---
IMBW, IANAL2, IMHO, IAVO
imaybewrong, iamnotalawyertoo, inmyhumbleopinion, iamveryold [ Reply to This | # ]
|
| |
| Authored by: webster on Friday, June 13 2008 @ 02:55 PM EDT |
..
PJ's message to the paper carries many truths, but it is relatively
uninteresting. It is complex with legal subtleties. As between the vengeful,
jerk lawyer and a "perverse" judge, it is far more interesting and
simple to out the judge.
If you want to catch the rapidly passing readers, you have to learn to
"think in headlines" and not much more. After all, a half-truth is
still a truth.
~webster~
...................Lot of judicial googling today --in Utah at least.
.[ Reply to This | # ]
|
| |
| Authored by: tknarr on Friday, June 13 2008 @ 03:08 PM EDT |
The first thing to remember about a Web site is that the site is the files
available, not the files available through links from pages. When you ask
the server for a directory, using a path ending in a "/" without a filename
after it, the server follows a search process. First, it looks for a file in
that directory like "index.html" or similar. If it finds it, it serves it up. If
it doesn't find that index file it generates a page containing a directory
listing of the contents of the directory, with each filename being a link to
that file, and serves that listing up. The consequence of this is that a Web
server's contents are by default public unless and until explicitly made
otherwise. Just because no page on the site links to a given file doesn't mean
someone can't find out that that file exists.
It's possible to configure
most Web servers so they won't serve up a default directory listing if they
can't find an index file, but one shouldn't depend on that for protection.
First, there've been notable bugs that allowed people to get the directory
listing even when it was disabled. Second, someone can simply guess probable
filenames, request them and see if they get a response or not. Many people use
predictable file names, if just because it's easier to remember them, so random
guessing may not need to be as random as it seems. For instance, many digital
cameras generate filenames of the form DSCnnnnn.JPG for photos,
and a lot of people just put the images up under those names and put descriptive
text in hyperlinks, so if I know someone's linked to DSC00035.JPG I might try
starting with DSC00001.JPG and working up to see which photos are
present.
The only way to truly make a Web site (or a portion of it)
private is to implement HTTP authorization on it. That means setting up users
with passwords on the server, and adding .htaccess files or the equivalent that
flag everything in or below a certain part of the filesystem (possibly starting
at the root of the document tree and covering all of it) as requiring a valid
username/password be presented before it can be served up regardless of how it
was requested. If you don't do this, then those files are public. If you don't
link to them, they're public. If you hide them behind a blank index page with no
links, they're public. If you don't advertise them, they're public. If they're
listed in robots.txt as not to be indexed, they're public. If you don't
like that, you know where to find .htaccess. [ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 03:31 PM EDT |
Lessig implies that there is no porn on the server. He specifically states that
there is nothing illegal. The only source of the "porn" meme is the LA
Times. As PJ discovered, the LA Times is not interested in fair and balanced
coverage. They just want to sell news papers, and "porn" sells. I see
no justification for propagating the "porn" meme until there are some
facts to back it up.
I think this is a tempest in a teapot and unworthy even of the LA Times, which
used to be a great paper.[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 03:37 PM EDT |
This is a case you might want to look at: Healthcare Advocates Inc. v. Harding
Earley Follmer & Frailey, No. 05-3524 (E.D. Pa. July 20, 2007). Opinion is
here:
http://substantialsimilarity.org/wp-content/uploads/subsim/2007/07/07d0852p.pdf.
It concerns access to the Internet Archive Wayback Machine despite the
deployment of a robots.txt file. The defendant accessed the archive and obtained
copies of files intended to be removed from the archive because the Archive
servers weren't functioning properly that day. The court said that obtaining
access because you got lucky doesn't violate the federal Computer Fraud and
Abuse Act. The analysis is of interest to the situation you have outlined.[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 03:39 PM EDT |
As I say, I'm no lawyer, but if that doesn't apply, could someone
please explain to me why it doesn't? I suppose you could defend by saying you
thought it was public, and that's just the flip side of what Kozinski is saying,
that he thought it wasn't.
Both could be and probably were true.
The default assumption on the Web is that anything that can be reached by typing
in a URL is public (that is, after all, its purpose). As that was evidently the
case with these files, how was the public to know that they were intended to be
private lacking even a "This is private" notice, let alone any authentication?
On the other hand, it is not hard to believe that the judge was sufficiently
ignorant of the way the Web works to believe that removing index.html was
effective security.[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 03:41 PM EDT |
To my way of thinking everything webby is open until it is closed.
If you want something closed, then put a lock on it - no matter how feeble. ie:
name = name & password = password
The Judge seems to have made no attempt to put a lock on his web door.
Keep in mind the history of the internet is open - the history of private
property is closed.
There have been court battles over deep linking - Guess who won![ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 03:43 PM EDT |
Seems somewhat similar to this: Healthcare
Advocates -- The Incredible "Lawyers as Hackers" Case
And PJ, I'll
answer your question about whether California Penal Code applies with another
question. Would you want it to apply? Should it really be a crime to
take a URL that someone sent out, remove the filename, then look at the
directory of an unprotected server? And before you answer, I'll quote you from
the above link:
See what's wrong with this law? Litigants don't
always stick to just what is reasonable. They go for whatever the law allows,
stretching as necessary to cover the facts at hand. It's something to think
about next time you say, "There oughta be a law." Think of the most extreme,
unpleasant and unreasonable litigant in the universe, and ask yourself, will
this proposed law enable really bad outcomes? Could it be misused against
innocent people?
My feeling is that if Judge Kozinski or his
son was smart enough to setup a robots.txt file to prevent indexing, they're
smart enough to add .htaccess files for either adding a password or disabling
indexing.
[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 03:50 PM EDT |
If you saw that message, would you assume that you were supposed to
monitor the site? That it was OK to enter and look around?
Yes, PJ, I
would consider it OK to "look around".
If you want to keep something
private, you don't expose it to the billion+ people who have access to the
internet. At a minimum, you protect access with a password. If it's really
important, you use https, not http.
[ Reply to This | # ]
|
| |
| Authored by: GLJason on Friday, June 13 2008 @ 03:52 PM EDT |
I don't think Lessig's analogy is quite right about the locked window, it's
more like a house with a window and an open door. Family and friends can use it
and it isn't actually protected by a password. It's still trespassing, but
maybe not breaking and entering. Maybe not even trespassing, maybe more like
sitting across the street and watching through the window with
binoculars.
There are close parallels to what IBM did with SCO in
finding that they were still distributing Linux. SCO's site was for customers
only and IBM shouldn't have had access, but they were able to get in and see
that SCO was still making Linux available in 2004 I believe. That seems to be
almost exactly what is happening in this case from what I've read.
[ Reply to This | # ]
|
- Siding with SCO for a change, PJ? - Authored by: Vic on Friday, June 13 2008 @ 09:04 PM EDT
- Butler? - Authored by: Anonymous on Saturday, June 14 2008 @ 09:09 AM EDT
- Butler? - Authored by: Vic on Saturday, June 14 2008 @ 09:36 AM EDT
- Butler? - Authored by: PJ on Saturday, June 14 2008 @ 10:28 AM EDT
- Butler? - Authored by: Vic on Saturday, June 14 2008 @ 10:41 AM EDT
- Butler? - Authored by: PJ on Saturday, June 14 2008 @ 11:00 AM EDT
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 04:11 PM EDT |
| Of course, by going to school and viewing the groklaw post about Computer
Security being an Oxymoron... we then have an understanding that any computer
network can be visited by those who have the tools and the desire to do so?
How? Who knows... But, you have to remember the Uni-Bomber was a somewhat of a
math expert, and so when you put this type of mind in front of a computer, feed
it a non-stop diet soda (see google about aspartame, serotonin, dopamine, etc
connection)... or even throw in a genetic twist called insanity. Well, the
computer network is then how secure?
Groklaw Comment about Security found here
See-
Article 6 Can Viruses Be Detected? by Jennifer Lapell at http://www.securityfocus.com/in focus/1267
( ? )... This
article is ONLY ONE of a dozen historical articles on computer security (or lack
of, if you get the drift) found listed in this comment link.
If the computer
server in question was Windows based (or even any other OS), if or not secured,
and then we get to the question of how secure is, is...? Well, do the
math.
This friend that cleans computers, I was there once when another
person brought in a computer, that was running slow, it ran windows but should
not have run that slow, and upon examination it had a Trojan virus, and deep
down in the system file area of the file structure it had sub-directories loaded
with all sorts of the worst bad video stuff out there, and it was happily
serving up those files to those that knew of this website to visit, via
backchannel access, by all sorts of slimy clowns. AND the owner of the
computer did not know anything about this? It was going on day and night, via
this broad band connection this person had!
If the law visited this same
person with a need to examine the computer, then hey, depending on the nature of
the examination of those files on the computer that were placed there by someone
else, then, how would this person then explain *that* to the average
judge/lawyer that does not know anything about computers to begin with. AND
worse, the average JURY is clueless as well.... SO. off to the Fed funded
"secure" Hotel you go for a long vacation where you can look forward to 3 hots
and a cot, and maybe, depending you get to be listed on one of those site
forever as well... Guilty as charged. Who is to be the wiser - hey those files
were on YOUR COMPUTER remember? Of course YOU could be the only one to put
them there, who else?
SO - the first rule of computer security
is:
1- Don't buy a computer.
The second rule kicks in if you do own a
computer...
2 - If you buy a computer, don't turn it on..
Now that my
friends, is computer security.
If you connect to the interent,
really how secure are those files, HOW SAFE DO YOU REALLY FEEL THAT YOU HAVE NOT
BEEN HACKED, and how many really know what kind of junk files that someone has
put on your system? And we are not talking about cookies!
Certainly this
files on a server on the internet, and wanting to secure them, gets way even
more amusing during Amateur Hour, as does America's home videos... maybe
examining folks home computers could be a new reality show? If aired, it would
either get lots of laughs, or it could increase the heart attack rate,
depending.
And the really funny thing is this... We are all amateurs, are we
not?
Remember the math, MIND like Uni-bomber (MULTIPLY TIMES) how many
billion internet users (PLUS) slow or high speed access to computer network =
Safety (yea, right)!
[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 04:18 PM EDT |
502.c.1.A Devise or execute schemes
I have only heard that he published links, not content, and publishing data
secreted by a public official is fair game. This site was not
"secure" if it had a robots.txt on it, and the robots.txt didn't work
anyway, google has info on its contents.
502.c.1.B wrongfully control data, again the guy only published the links, didnt
sell, etc., so where is "wrongful control" in that.
502.c.2 again he published links as to where data was. and it was not secured,
502.c.3 this arguably is a problem if you count that he probably caused a DOS
attack on the site by publishing it. but that in this case was not a planned
action, so the loss of computer services is only due to the "Digg" or
Slashdot affect, and will abate.
The judge or anyone should never attach a computer to the internet if the data
on is not something you wish to shout to the corners of the earth, if there are
accessible areas on it.
If I am invited in to a library to look around and suddenly find that a door
that was not properly locked opens onto a room full of steamy sex displays going
on, am I to be prosecuted. If the room is discovered in the course of a
burgularly or other felony, yes, but having a registered domain invites entry.
robots.txt is like posting a sign saying "private library, dont publish our
card catalog or a map of our contents" but you are invited to look
around.
[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 04:21 PM EDT |
I remember our discussion in the SCO vs. IBM case, where IBM downloaded certain
"private" files from SCO's website. The protections were silly (empty
password), but the site did warn no to download things unless you were a
customer (doesn't help SCO from a legal standpoint).
I'm not saying that it is always right or always wrong to view published files
that a person thinks have been protected -- it's a complicated issue.
But it does seem like there is an inconsistency here, and an analysis deeper
than the one presented is in order.
[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 05:33 PM EDT |
| His Honer is still a perv, as they say in this country .. :) [ Reply to This | # ]
|
- still a perv .. - Authored by: Anonymous on Friday, June 13 2008 @ 06:23 PM EDT
- still a perv .. - Authored by: Anonymous on Saturday, June 14 2008 @ 05:22 PM EDT
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 05:51 PM EDT |
I posted a question on this as an OT in the previous story
last night (our time) and after a good night's sleep on this
side of the sea, I find it has blown up to a whole story with
the full wisdom of Groklaw examining all nooks and crannies.
It seems we are assigning contributory negligence to both
parties to this sorry saga. I have some experience running
a webserver on which I have both public pages intended to
be read by all and sundry, and "semi-public" pages which are
not visible through the analogous window, but I give some
occasional viewers a url, or analogous room number. I have
"Go Away" index.htm pages, and I've been lazy, and lucky,
in not bothering with administering .htaccess, the analogous
door keys. Client domain restriction is not worth it because
of dynamic IPnrs and spoofing.
I know which search bots see robots.tx and go away, and which
stop to read robots.txt and obey the instructions therein, and
which ones take no notice at all and tramp thru wherever
they find a link. Which is why there are no links to some things.
Our campus Computer Science dept. has an annual project
where students build a search bot and are marked on how well
it obeys, or not, robots.txt. That's an eyeopener in the logs.
What I don't see yet is what breed of server Kozinski is using,
some are easier to fool than others, and how did Sanai find
what he found? And what did he find? There are suggestions
that some of the material on Kozinski's page was only links, in
which case it becomes a "making available" question. I fear
that any judicial inquiry won't be interested in these
technical details.
And I restate the most important question: should we let
judges believe that running a website is as simple as
running a kitchen cupboard?
[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 07:05 PM EDT |
It seems to me that search engines must be constantly snooping through
directories that are never published. I have on a number of occaision taken to
entering a URL that was up a directory or for a sister directory that I thought
might be interesting. Just looking around through linux distributions, another
counties weather. If I didn't trigger a warning or password protection I didn't
care. Of course I am probasbly always breaking some law by some draonian
interpretation. I expect such methods would be problematic for admissible
evidence.
Hopefully this judge is protected by the constitiution. The liftime appointment
is designed to provided judges releif from bullying. In a way I am relieved
that the judge made this mistake. I think it will prove very instructive at
very little cost. I am also relieved that the rest of us mere mortals may be
viewed with a little more compassion.
If the judge or ninth circuit made a sound decision in the divorce case, it will
bear the scrutiny and reflect poorly on the instigator. If not, well it may be
worth it. [ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 07:33 PM EDT |
| See Seth Finkelstein's blog entry How
"alex.kozinski.com" worked.
[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 07:45 PM EDT |
Anything that you put on the web, unless it's specifically password-protected,
is public.
If it were the other way around, you could find yourself committing offenses
every day by simply accessing pages via Google that the site owner did not mean
to be indexed.
> But this was a private file server, like a private room,
> hacked by a litigant with a vendetta.
No. For the same reason, ridiculous "disclaimers" like "If you
are a member of the police or the government, you may not enter this
(warez/porn/etc.) site" are legally void.
I am especially wondering why you are equating access to files that are not
directly linked with hacking.
Don't you remember how ridiculous you considered SCO's allegations that IBM
"hacked" into their FTP site because it was (if ever so weakly)
password-protected (anonymous/email adress)?
If you consider accessing an FTP site behind a password (however simple access
may be factually) "free game", why do you think accessing files or
directory structures that are not even protected in any way is worse (either
morally or legally)?
__
magicmulder[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 07:52 PM EDT |
A better analogy is that he has a huge panoramic picture window that gives any
passerby a look into the full contents of the house.
For a couple of years, yeah, he had a sign on the street pointing at his house
saying "FREE SHOW!".
Later, he decided that he didn't want to publicize his shenanigains, so he tood
down the sign and he taped a little note saying "please don't peek
inside".
But at NO point did he ever remove the contents (delete), install a shade
(firewall / login), much less secure it with a lock (cryptography).
His site is public.
Claiming an expectation of privacy fails.[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Friday, June 13 2008 @ 08:35 PM EDT |
This guy sounds like a stalker to me. And a creepy one at that. I think the
judge was right to recuse himself, though, if only to get out of the public
eye.
That said, I'd be VERY leery of prosecuting or attempting to prosecute someone
for viewing a directory listing.
Otherwise, stuff like that will appear in boilerplate warnings on every page and
it's just too low a bar for something that's supposed to separate the legal from
the illegal.
Mind you, I'm not basing that on what the law is (I don't know it all that
well), but what I think the law should be.[ Reply to This | # ]
|
| |
| Authored by: joe7pak on Friday, June 13 2008 @ 11:52 PM EDT |
Does somebody get the sense that some astroturfing is going on here? Just at the
top level of comments, these seem to be written by the same person - same basic
thought, same point, same structure of message. What follows are a line from
each comment, just at the top level, mind you, that have this sameness - search
for them and tell me I'm wrong.
"There can be no privacy expected on a publicly accessible website.
....."
"If you want something private, and keep it on the Web,...."
"To my way of thinking everything webby is open until it is
closed......."
"Yes, PJ, I would consider it OK to "look around"......"
"I have only heard that he published links, not content, and publishing
data secreted by a public official is fair game....."
"Anything that you put on the web, unless it's specifically
password-protected, is public....."
"A better analogy is that he has a huge panoramic picture window that gives
any passerby a look into the full contents of the house....."
[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Saturday, June 14 2008 @ 12:12 AM EDT |
Most of the pages on the unofficial fan site
http://notabug.com/kozinski/
now return a custom 404 page.[ Reply to This | # ]
|
| |
| Authored by: maz2331 on Saturday, June 14 2008 @ 12:18 AM EDT |
I'm wondering how many of the photos/videos or other files are copyright
infringements?
Actually, I'm not taking a side here, and think that the judge has been
seriously wronged by the whole affair.
But it does have the possibility to point out to everyone just how insane and
inane the entire copyright regime has become.
I also fail to see why it's an issue to begin with if he had some
"pr0n" on a website. "Community standards" CAN include that
which judges personally find acceptable, as well as the general public. Or are
"community standards" only really meant to mean "standards of the
most uptight and prudish members of the community?"
My guess is the latter.
[ Reply to This | # ]
|
| |
| Authored by: Alan(UK) on Saturday, June 14 2008 @ 11:08 AM EDT |
There has been lots of comments referring to: analogies, US and other law, and
morality.
The thing to remember is that when the judge put something in that place, on
some server, somewhere, that he considered to be his own piece of private
property, he was putting it in a place connected to the whole world via the
Internet. He even put it in a place with his surname as the domain name.
Analogies are no help here, some just do not work across international
boundaries, ditto law and morality. 'No Trespassing' seems as good an example of
this confusion as any.
In this country, if you have a secret, dirty or otherwise, you try to keep it
that way. As for, 'Ain't nothin' here - Y'all best be movin' on, compadre'? What
is that supposed to mean? Sounds like an invitation to me, but others think
differently, the man is a judge after all, he ought to be able to express
himself coherently.
Once someone, somewhere, puts a link to one of the judge's sooper seekrit pages,
they are not secret any more, anyone might go there without even realising that
it is: bringing the judiciary into disrepute; demeaning to men, women, and
domesticated animals; and corrupting public morals.
The judge's real complaint is that he has been found out.
The Internet is something new, it really grew by popular demand rather than the
result of long deliberation by governments, academics, and theologians, at
international conferences. Trying to establish Internet law and ethics by
analogy with existing institutions is bound to fail. We have been through all
this before with the printing press, the postal service, theatre, cinema, radio
and television - but this is the big one, the real shifter of paradigms.
We have seen all of these controlled by by various powers, the King, the
Postmaster General, the Lord Chamberlain, the British Board of Film Censors, and
the BBC. Now, along comes this upstart, the Internet, that does not want to
answer to anyone. You cannot stone it for working on a Saturday (cannot even
define Saturday), you cannot imprison it in the Tower, it is a wild, heathen,
outlaw. Copyright laws, made for the printing press, stretched to cover
gramophone records and even software, is now strained to breaking point. If the
Internet came into existence before the printing press, what copyright laws
would we have? How would freedom of the press be enshrined in the constitution
(written or otherwise)?
We have, like it or not, been uprooted from our former safe little worlds and
dumped into a global village. Over here, we have not even come to terms with
being European.
Perhaps the future lies with the children, those able to access all the
functions on a mobile phone.
---
Microsoft is nailing up its own coffin from the inside.[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Saturday, June 14 2008 @ 03:37 PM EDT |
I notice a couple of memes repeating here, first
privacy != security
but I posit that the converse is true, security == privacy
So you set robots.txt, a dummy index page, noindex=true
and you get privacy. To the level, since analogies seem in order,
of a latched gate, or a shut, not locked, door with a sign saying
"No Entry". If someone enters we have a moral transgression.
There might be laws against it where you live, that's local custom.
This analogy was taken further in one post that suggested
when you open the door the butler asks "What do you want?"
You ask for the copy of Rabelais that is on the kitchen shelf
with the cookbooks. He goes away, comes back and says
"Sorry Sir, we don't have that here". You then ask for a copy
of Balzac from the same place, and this time he gives it to you.
That's how webservers work. The analogous butler has no
moral sense, of whether French novels should be among
the cookbooks, or whether you are entitled to it.
Unless he has been told who is allowed to have the
French novels, or anything from the kitchen shelf.
If you want security you have to lock the door, set access
restrictions on the directory, ask for a [ key | password ].
Secondly I see above a frequent analogy that webadmin
[ is | is not] as easy for Joe Sixpack as driving a car.
I see the negative side of this one every day at my job, with
highly skilled professional musicians unable to perform
"simple" tasks on their desktop computers. Because they
are not practising, performing, these tasks every day they
forget. For a family website like Kozinski's, how often
would the admin settings need adjusting? Once or twice
a year? Maybe never if it was done right first time?
Practice makes perfect. Someone who opens a command
line terminal at least twice a day will do webadmin in
their sleep. I open a cli more than twice a day, and
nine out of ten of my office colleagues could not
administer a webserver with a gui.
The investigation may disclose whether Sanai "hacked"
or circumvented any technical measures on the server.
But it may not dwell long on the question of Kozinski's
technical competence in securing his material.
The justices will concern themselves with moral questions
like Kozinski's reasons for keeping that material in such
a place, and Sanai's motives in disclosing it.[ Reply to This | # ]
|
| |
| Authored by: Anonymous on Sunday, June 15 2008 @ 02:03 AM EDT |
Ok, so we're not supposed to discuss politics here right? I think PJ is showing
some bias by trying to make the case that anybody going to
http://www.groklaw.net/stuff (a non published link) would be violating the law.
If the contents of a directory are intended to be private, then the content
owner or moderator should put an htpasswd file in place no? Better yet, get the
content off the INTERNET alltogether. The purpose of a network is to move data
between computers. The Internet is a public network. If you're running a
public site, you must expect that all content there can be viewed unless you put
some security measure in place. No security measure was in place on Kozinski's
site.
What about the content itself? Would an average american find images of a man
being pursued by an aroused donkey offensive? I would argue that many would.
It may even cross into the realm of the obscene. In any case, it is highly
relevant to the case the judge is presiding over and he did the right thing by
declaring a mistrial today.
[ Reply to This | # ]
|
| |
| Authored by: stingbot on Sunday, June 15 2008 @ 12:35 PM EDT |
With respect to this:
"You can read about what they each, Kozinski and Sanai, wrote on a dispute
between them here. It raises a question in my mind about whether or not this is
just about the divorce. But my next question would be, if this was intended as a
private site, would it be legal for an uninvited person to enter and monitor it?
Exactly how would that work, given the Computer Fraud and Abuse Act, not to
mention any local California laws regarding privacy and computer integrity? We
know there are such laws in California, from the HP-reporters scandal."
Does that give ammo to SCO's accusation that IBM "Hacked" their ftp
site?
It really seems silly. Put something on the web, expect it to be public. If
you need to protect it, don't put it on the web.[ Reply to This | # ]
|
| |
| Authored by: kattemann on Monday, June 16 2008 @ 11:33 AM EDT |
Just a tip: If you send an e-mail as plain text, no HTML, it's less likely to be
filtered as probable spam. Part of my job here is to go through the spam bucket
several times a day and override or agree with the filter, and just about all
the non-spam messages there are HTML or worse.
kattemann[ Reply to This | # ]
|
| |
| Authored by: BassSinger on Tuesday, June 17 2008 @ 02:37 PM EDT |
Just a note on a possible way subdirectories on this website could have been
accidentally left open (it happened to me).
If you are running a Microsoft server (at work, I wouldn't do that at home),
there is a check box for forcing all access through the top (login) section of
the website. However, if you add a subdirectory after setting the check box it
is *NOT* protected by this "feature". So it makes you think you are
safe, while leaving the barn door wide open. What a wonderful security system.
The safest, according to M$.
Oh, if you uncheck the box and check it again it will protect all subdirectories
extant at that time.
In a Chord,
Tom[ Reply to This | # ]
|
|
|
|
|



